
unleash your future tech



About Hackanics
Hackanics offers over 50 practical courses designed for cybersecurity professionals at all levels.
From foundational concepts to advanced leadership techniques, our courses are crafted to equip you with skills you can immediately apply in real-world scenarios.
Whether you’re just starting out or aiming for leadership roles, we have the resources to help you advance in your career.
Here are reasons why choose us:
- Expertise and Experience
- Cutting-Edge Technology
- Customized Solutions
- Proactive Threat Mitigation
With these various reasons, we are the best choice to ensure strong and reliable cybersecurity training to your students
why learn our courses?
Over a lakh of people fall victim to cyber attacks
Cross-Site Scripting (XSS)
Attackers inject malicious scripts into trusted websites, which then execute in the browsers of users who visit those sites. This can lead to unauthorized actions, data theft, or the distribution of malware.
SQL Injection (SQLi)
Occurs when attackers manipulate a database query through unvalidated input, often compromising the entire database.
Threat Detection and Response
Happens when sensitive information, such as passwords or financial data, is improperly secured, leading to potential data breaches.
Cross-Site Request Forgery (CSRF)
ricks authenticated users into executing unwanted actions on a web application, potentially leading to unauthorized transactions or changes.
Server-Side Request Forgery (SSRF)
Exploits a server’s ability to make requests to internal or external systems, often bypassing firewalls and accessing internal services.
Insecure Deserialization
Allows attackers to manipulate serialized objects to execute arbitrary code, potentially leading to remote code execution or privilege escalation.
Secure Your Present, Protect Your Future with Hackanics
Cyber threats are evolving—are you ready to defend against them? Gain hands-on skills, industry-recognized certifications, and expert guidance to advance your cybersecurity career.
Master Cybersecurity with Our Courses
Empowering Security, Protecting Your Digital World.
In today’s rapidly evolving digital landscape, protecting your business is more critical than ever. At Hackanics, we combine industry expertise with innovative technology to offer comprehensive cybersecurity solutions and training that empower your organization to stay ahead of threats. Our commitment is to secure your present while building a resilient future for your business.

The goal of the course is to provide students with advanced knowledge and useful skills in cybersecurity and ethical hacking.

Students who want to learn advanced ethical hacking tactics and strategies can enroll in the Ethical Hacking Mastery course.

The Advanced Executive Course on Cybersecurity is tailored for senior executives, managers, and professionals seeking an in-depth understanding of cybersecurity challenges and strategies

Bug Hunting course, you can take an exciting trip into the world of cybersecurity and learn how to find and fix vulnerabilities that pose a threat to digital landscapes.
Services
Cybersecurity Services
Managed IT Security

- Network & Application Penetration Testing
- 24/7 Security Monitoring & Threat Detection
- Incident Response & Risk Management
Bootcamps & Certification Prep

- Intensive Cybersecurity Bootcamps
- Practice Tests & Exam Readiness
- Job-Oriented Learning Paths
College Training Programs

- Ethical Hacking & Cybersecurity Workshops
- Hands-on Labs & Real-World Simulations
- Industry-Recognized Certifications
Corporate Training & Upskilling

- Cybersecurity Awareness for Employees
- Advanced Training for IT Teams
- Red Team vs. Blue Team Exercises




Testimonials
See What Our Clients Have to Say
FAQs
Unlocking Cybersecurity Knowledge
Fusce vehicula dapibus ipsum at finibus. In rhoncus, nunc non laoreet tempor, urna libero bibendum sem, et luctus ex metus quis ipsum.
The best setup is to use Kali Linux or Parrot OS (VMware/VirtualBox image) as your main attack machine and Metasploitable as the vulnerable target. For web security testing, add Burp Suite (Community or Professional). Always run them inside isolated virtual machines to stay safe and avoid affecting your main system.
The top platforms include PortSwigger Web Security Academy (web vulnerabilities), HackerOne (real bug bounty programs), TryHackMe (guided labs), Hack The Box (realistic hacking machines), OverTheWire (Linux/network basics), Root-Me (multi-category challenges), and VulnHub (offline vulnerable VMs).
Common tools include Nmap (network scanning), Metasploit (exploitation), Burp Suite (web testing), Wireshark (traffic analysis), SQLmap (SQL injection), Hydra (brute-force), and Aircrack-ng (Wi-Fi security).

Blog & Articles
Read Our Latest Blog & Articles
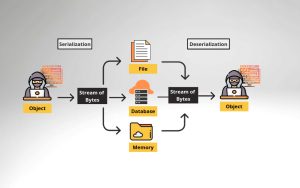
Insecure Deserialization
What is Insecure Deserialization? Instagram X-twitter Youtube Insecure Deserialization is a security flaw that happens when an application loads (deserializes) data from an untrusted source without checking it, allowing attackers to modify the data and potentially gain unauthorized access, change
Server-Side Request Forgery (SSRF)
What is Server-Side Request Forgery (SSRF)? Instagram X-twitter Youtube Server-Side Request Forgery (SSRF) is a web vulnerability that allows an attacker to make a vulnerable server send unauthorized requests to internal or external resources, potentially exposing sensitive data or enabling
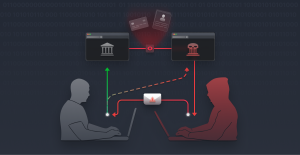
Cross-Site Request Forgery
What is Cross-Site Request Forgery (CSRF)? Instagram X-twitter Youtube CSRF tricks an authenticated user into unknowingly performing actions on a web application. Since most browsers automatically include session cookies with requests, the forged request appears legitimate to the server—even though
Contact Us
We Are the Perfect Cybersecurity Training Partner
In today’s digital era, staying ahead of cyber threats starts with empowering your team. At Hackanics, we specialize in providing top-tier cybersecurity training that equips colleges and corporates with the skills needed to secure the future. Our programs are designed to turn cybersecurity challenges into opportunities for growth and innovation.
- Expertise and Experience
- Customized Training Solutions
- Proactive Threat Preparedness
- Proactive Threat Mitigation
Let Hackanics be your trusted partner in building a resilient and skilled cybersecurity workforce.
Try These Commands to Check your browser Vulnerability
Try These Commands:
- scan - Check for vulnerabilities
- encrypt - Learn about data encryption
- decrypt - Understand data decryption
- clear - Clear the terminal
Type a command and get a free cybersecurity tip!
