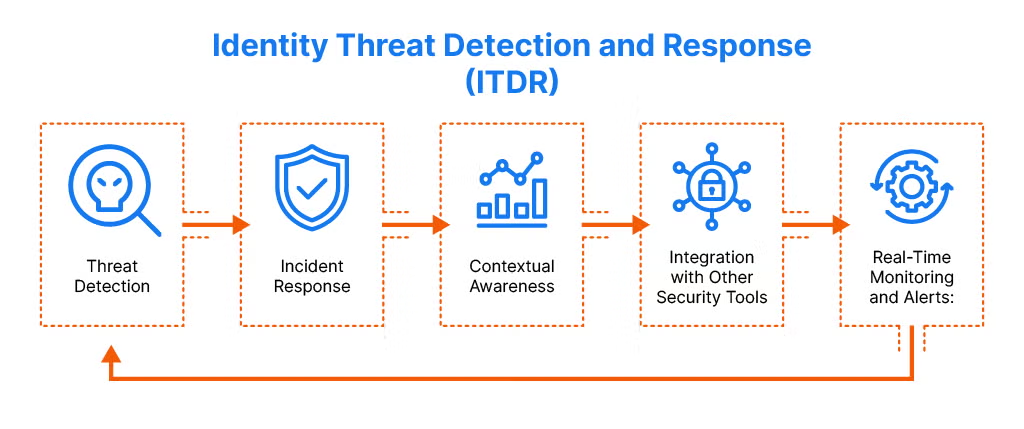
Threat Detection and Response (TDR) is a cybersecurity process focused on identifying, analyzing, and responding to cyber threats that target an organization’s digital environment. It’s designed to detect both known and unknown threats — including highly evasive malware — and take swift action to contain and neutralize them
In today’s digital landscape, cyberattacks are more sophisticated and frequent. TDR plays a vital role in:
It’s especially crucial for organizations with complex IT environments, cloud infrastructure, or remote workforces.
SIEM systems collect logs and security data from various sources like firewalls, servers, applications, and network devices. This data is then analyzed to identify suspicious activity through correlation rules, analytics, and behavior patterns.
Key Features:
Centralized log management
Real-time alerting and dashboards
Correlation rules to detect attacks
Compliance reporting (e.g., PCI-DSS, HIPAA)
Use Case:
If multiple failed login attempts are detected from different countries within a short period, the SIEM raises an alert for a potential brute-force or credential stuffing attack.
Examples:
Splunk
IBM QRadar
ArcSight
LogRhythm
EDR focuses on monitoring endpoint activity (files, processes, registry, memory, etc.) and detecting anomalies or malicious behavior.
XDR integrates not only endpoint data but also network, email, and cloud data for a broader, unified view.
Real-time threat detection on endpoints
Threat hunting capabilities
Incident response actions (e.g., isolate endpoint, kill process)
Automated response across multiple vectors (in XDR)
If ransomware starts encrypting files, EDR can detect unusual file access patterns and automatically isolate the infected endpoint.
CrowdStrike Falcon (EDR)
SentinelOne
Microsoft Defender XDR
Palo Alto Cortex XDR
SOAR platforms integrate with SIEMs, EDRs, and other tools to automate incident investigation and response workflows.
Key Features:
Playbook-based automation (e.g., auto-block malicious IPs)
Case/ticket management
Human-machine collaboration
Integration with threat intelligence
Use Case:
When a phishing email is detected, SOAR can automatically extract the sender’s IP, check it against threat intel feeds, block it in the firewall, and open a ticket in the helpdesk system.
Examples:
Palo Alto Cortex XSOAR
Splunk SOAR (Phantom)
IBM Resilient
Swimlane
TIPs gather, normalize, and enrich threat data (like IOCs and TTPs) from internal sources, commercial feeds, open-source intelligence (OSINT), and partners.
Key Features:
Aggregation of multiple threat feeds
Enrichment of alerts with context (who, what, why)
Threat scoring and prioritization
Integration with SIEM/SOAR for automated responses
Use Case:
If a SIEM alert includes an IP address, the TIP can provide context such as its association with a known threat actor or past incidents, helping analysts triage faster.
Examples:
MISP (open-source)
Anomali ThreatStream
ThreatConnect
Recorded Future
Malware refers to any malicious software—such as viruses, worms, trojans, and spyware—designed to disrupt, damage, or gain unauthorized access to systems, while ransomware is a specific type of malware that encrypts a victim’s files and demands payment (usually in cryptocurrency) for the decryption key.
TDR tools detect these threats by analyzing suspicious file behavior, identifying known malicious signatures, monitoring system changes, and using behavior-based analytics to flag zero-day variants.
Phishing attacks trick users into revealing sensitive information—like passwords or banking details—through deceptive emails, websites, or messages, while social engineering manipulates people into bypassing security practices.
TDR tools identify these threats by analyzing email metadata, scanning for malicious links or attachments, monitoring user behavior, and flagging abnormal access patterns or credential use.
Insider threats arise when employees, contractors, or partners—either maliciously or unintentionally—cause harm to the organization by leaking data, abusing access, or sabotaging systems.
TDR platforms detect these threats by monitoring user behavior (User and Entity Behavior Analytics – UEBA), identifying unusual access patterns, privilege misuse, data transfers, or off-hours activity that deviates from normal baselines.
Advanced Persistent Threats are highly sophisticated, targeted attacks—often orchestrated by nation-states or organized groups—that infiltrate systems and remain undetected for extended periods to steal sensitive data or disrupt operations.
TDR systems detect APTs using threat intelligence, anomaly detection, endpoint telemetry, network traffic analysis, and by correlating low-level indicators across time to uncover the multi-stage, stealthy nature of these attacks.
What Happened:
Swiss banking giant UBS was impacted by a cyberattack targeting one of its external service providers, Chain IQ. The attack led to a data leak involving UBS employee information, but no client data was affected. READ MORE
Data Exposed:
Employee names
Email addresses
Phone numbers
Office locations
Internal HR data
A high-ranking UBS executive’s contact details were also found on the darknet.
Threat Detection and Response:
UBS responded swiftly, identifying and containing the breach.
Investigations confirmed no impact on client-facing systems or financial data.
Coordination occurred across multiple organizations as Chain IQ serves many major clients.
TDR Lessons:
Third-party vulnerabilities are a major threat vector—even when internal systems are secure.
Fast detection and containment prevented broader damage or reputational loss.
Employee data leaks can fuel phishing, impersonation, or insider threat campaigns.
Impact:
Only employee data leaked—not customer or financial records.
Demonstrates successful TDR handling in a highly regulated financial environment.
What Happened:
WestJet, a major Canadian airline, was hit by a cyberattack in June 2025. The attackers targeted the airline’s internal IT systems, causing disruptions to their website and mobile app, although flight operations continued without interruption. READ MORE
Detection and Response:
The cyber threat was detected by WestJet’s internal cybersecurity team, triggering a full incident response protocol.
Law enforcement, including the Royal Canadian Mounted Police (RCMP), were involved in the investigation.
WestJet worked with cybersecurity experts to isolate affected systems and restore digital services.
Impact:
Customers experienced temporary issues with online booking, check-ins, and app functionality.
No passenger data or financial information was reported as compromised.
Core airline functions like flight schedules and safety systems were not affected.
TDR Lessons:
Strong detection capabilities can prevent operational disruption even when digital assets are attacked.
Rapid coordination with law enforcement helps in investigation and risk mitigation.
Segmentation of critical systems (e.g., flights vs. apps) helped maintain continuity of service.
What Happened:
A targeted social engineering attack allowed cybercriminals unauthorized access to internal systems of global venture capital firm Insight Partners. READ MORE
Data Exposed:
Investor tax records
Fund management documents
Portfolio company bank details
Employee personal and HR data
Threat Detection and Response:
Detected by internal cybersecurity tools
Immediate account lockouts and isolation
Engaged law enforcement and third-party forensic experts
Notified affected individuals and organizations
TDR Lessons:
Social engineering remains a major risk vector
Real-time logging and monitoring are critical
Transparent communication is essential for trust recovery
Impact:
No business shutdown, but reputational damage risk
Sensitive financial and personal data leaked
Ongoing security audits and legal reviews
What Happened:
A cyberattack disrupted the internal IT systems of UNFI, a major food distributor, affecting supply chain and inventory operations. READ MORE
Data Exposed:
No confirmed data exfiltration, but logistics and operational systems were temporarily disabled.
Threat Detection and Response:
Detected via internal anomaly detection tools
Engaged FBI and cybersecurity partners
Manual workarounds kept operations running
Systems restored progressively
TDR Lessons:
Supply chain infrastructure must have strong cyber resilience
Offline contingency planning is crucial
Third-party and physical systems need protection too
Impact:
Delivery delays across grocery chains
Short-term stock outages in stores
Minimal data loss, but operational disruption
What Happened:
A small group of journalists covering China were targeted in a suspected state-sponsored cyberattack, compromising their work email accounts. READ MORE
Data Exposed:
Emails and contacts of affected reporters
Potential confidential source information
Threat Detection and Response:
Alert from Microsoft on suspicious activity
Password resets and MFA strengthened
Federal investigation launched
No signs of content alteration or broader access
TDR Lessons:
High-profile individuals need extra cybersecurity layers
Account-level TDR is just as critical as system-level
Awareness and training help prevent credential-based attacks
Impact:
No disruption to publishing or site operations
Risk of source exposure and targeted surveillance
Prompt action minimized long-term damage
Read More :
Signup our newsletter to get update information, news, insight or promotions.
Copyright 2025 © Hackanics