A phishing attack is a cybercrime in which attackers impersonate legitimate organizations or individuals to deceive victims into providing sensitive information. This often includes login credentials, credit card numbers, bank account details, or personal identification information. The attacker typically uses fake emails, websites, text messages, or phone calls that appear authentic to lure the victim into clicking malicious links or downloading harmful attachments. Once the victim interacts with the fraudulent content, their data may be stolen, their accounts compromised, or malware installed on their device. Phishing is one of the most common and dangerous forms of social engineering used in cybersecurity breaches today.
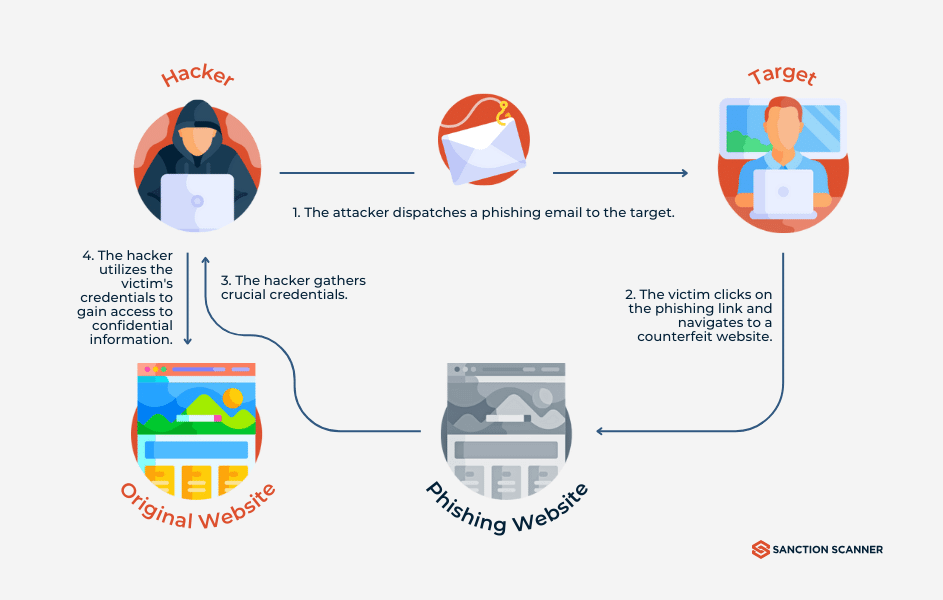
A phishing attack starts when a cybercriminal decides to trick a user into giving away confidential information, such as passwords, credit card numbers, or security codes.
The attacker carefully crafts a fake message — often an email, but sometimes a text message or even a phone call — that looks like it’s from a trusted company, such as a bank, delivery service, or employer.
This message includes a link that leads to a fake website, which is designed to look almost identical to a legitimate login page — such as PayPal, Facebook, Gmail, or a company portal.
The victim, thinking the site is real, enters their login credentials or personal information, which is immediately captured and stored by the attacker.
In some cases, the phishing page also uses scripts or reverse proxies to steal session tokens and cookies, allowing the attacker to log in without even knowing the password — a method that can bypass two-factor authentication (2FA).
Alternatively, the phishing email might include an attachment — such as a fake invoice, shipping receipt, or job offer — that, when opened, installs malware on the victim’s device, such as keyloggers or remote access tools.
Once the attacker has the stolen data or access, they can log into the victim’s accounts, make unauthorized purchases, transfer money, send more phishing emails from the victim’s account, or move deeper into a company network.
Some phishing attacks are broad and automated (called mass phishing), while others are highly targeted (spear phishing), designed specifically for high-value individuals like CEOs or finance officers (whaling).
To avoid phishing attacks, users should carefully check the sender’s email address, hover over links to see where they really go, avoid opening unexpected attachments, and always enable strong two-factor authentication where possible.
A phishing attack proof of concept starts with a security researcher using a tool like ZPhisher to clone a legitimate login page, such as Google or Facebook. The tool automatically generates a fake login page and hosts it using a tunneling service like Ngrok, which creates a public link to the cloned site. The researcher then simulates sending this link to a test user, for example, with a fake warning message like “Your account has been locked, please verify your identity.” When the test user clicks the link, they are taken to the fake login page that looks almost identical to the real one. If the user enters their login credentials, those details are captured and displayed in the researcher’s terminal, proving that the phishing setup works. This demonstration helps illustrate how easily people can be tricked and is often used in cybersecurity training or red team exercises to raise awareness and test defenses.
There are three main types of Phishing attacks. These are:
1). Email Phishing: – The most common type, where attackers send fake emails that appear to come from trusted companies to trick users into clicking malicious links or opening dangerous attachments.
2). Spear Phishing: -A highly targeted attack where the hacker customizes the message for a specific person or organization, often using personal information to make the email seem more legitimate.
3). Whaling: – A form of spear phishing that targets high-level executives or VIPs (like CEOs or CFOs), usually with fake legal notices, invoices, or urgent financial requests.
4). Smishing (SMS Phishing): – Instead of email, the attacker sends a fake message through SMS, pretending to be from a bank, delivery service, or government agency, urging the victim to click a link or call a number.
5). Vishing (Voice Phishing): – The attacker calls the victim on the phone and pretends to be someone trustworthy, like a bank representative or tech support, to steal personal information or credentials.
6). Clone Phishing: – A real, legitimate email is copied (cloned), but the original attachment or link is replaced with a malicious one. It often appears as a “resend” or “updated version” of the original.
7). Business Email Compromise (BEC): – An attacker either spoofs or hacks a company email account to impersonate a real employee (often someone in finance or leadership) and tricks others into transferring money or data.
8). Pharming: – Instead of using fake emails, this attack redirects a user from a legitimate website to a fake one by poisoning DNS records or exploiting browser vulnerabilities.
9). Angler Phishing: –Happens on social media platforms where attackers create fake customer service accounts and trick users into giving out private info via direct messages or fake links.
10). HTTPS Phishing: –Attackers use “secure” HTTPS websites with padlocks in the URL bar to make their fake sites look legitimate and trustworthy, tricking victims into ignoring other red flags.
The email may look like it comes from a trusted company, but when you look closely at the sender’s address, it’s slightly off — for example, support@paypa1.com instead of support@paypal.com. Attackers often use typosquatting or strange domains to mimic real companies.
Phishing emails often try to scare you into acting quickly by saying things like “Your account will be suspended,” or “Immediate action required.” This urgency is used to pressure you into clicking a link or entering information before you have time to think critically.
Many phishing messages contain obvious spelling, grammar, or formatting errors. These mistakes can be a red flag that the message is fake or was not sent by a professional organization. Legitimate companies usually proofread their communication carefully.
The link text in a phishing message may say one thing (like https://paypal.com), but when you hover over it, the actual URL is something completely different (like http://malicious-site.ru/login). Always hover over links before clicking to verify where they actually lead.
Phishing emails often include attachments you weren’t expecting (like invoices, receipts, or shipping notices), or links to login pages you didn’t request. These attachments may contain malware, and the links often lead to fake login forms designed to steal your credentials.
Bypasses 2FA by stealing tokens and session cookies
Uses phishlets (scripts to mimic real logins)
Transparent login relay (user doesn’t suspect anything)
Example Use:
A red teamer sets up Evilginx2 targeting Microsoft 365. The victim logs in through the real-looking page, but Evilginx2 intercepts and stores their session cookies, allowing the attacker to bypass 2FA and hijack the account without ever needing the password again.
Web interface for managing campaigns
Custom emails, landing pages, and tracking
Generates real-time reports and dashboards
Example Use:
An IT team launches a phishing awareness campaign with GoPhish, sending fake emails that look like HR messages. Some employees click the link and are taken to a simulated login page. The results are tracked, and those who fell for it are enrolled in security training.
.4). Social-Engineer Toolkit (SET)
Website cloning
Email spoofing
USB payload creation
Credential harvesting
Example Use:
In a red team engagement, a tester uses SET to clone a SharePoint login page and sends a fake email to employees saying, “Please upload the Q3 report.” The link leads to a cloned login page, and entered credentials are logged in real time.
Captures credentials and real-time 2FA tokens
Transparent page rendering
Supports real logins with fake data capture
Example Use:
During a red team test, Modlishka is set up to target Okta. A user logs in thinking they’re at the real Okta portal, but Modlishka proxies the request and logs the full session, including the temporary token, allowing a full bypass of multi-factor authentication.
British retailer Marks & Spencer faced a ransomware attack in 2025, leading to significant operational disruptions and a projected financial impact of £300 million. The attack, attributed to the cybercriminal group DragonForce, also resulted in the theft of some customer data, highlighting vulnerabilities in the retail sector’s cybersecurity defenses.
In September 2024, outsourcing company Infosys McCamish Systems announced a major data breach potentially affecting 6.5 million records. The breach, which dated back to late 2023, involved attackers being active within the system between October and November before detection.
Cybercriminals have begun leveraging AI to craft highly personalized phishing emails targeting corporate executives. These AI-generated messages mimic the tone and style of legitimate communications, increasing their effectiveness and making them harder to detect. Companies like Beazley and eBay have reported an uptick in such attacks, emphasizing the need for advanced detection strategies.
The cybercriminal group Scattered Spider executed sophisticated phishing and social engineering attacks against major casino operators. By impersonating IT support staff, they deceived employees into revealing credentials and one-time passwords, bypassing multi-factor authentication. This led to significant disruptions in MGM Resorts’ operations and a $15 million ransom payment by Caesars Entertainment.
In November 2022, Dropbox experienced a data breach after employees were targeted with phishing emails impersonating CircleCI. The attackers tricked employees into entering their credentials on a fake login page, leading to unauthorized access to 130 GitHub repositories containing API credentials and other sensitive data.
When a phishing attack tricks someone into revealing personal details — like their name, address, date of birth, Social Security number, or login credentials — attackers can use that information to impersonate the victim, apply for loans, open fraudulent accounts, or commit other crimes in their name. This can have long-lasting consequences for the victim, including legal issues and credit damage.
Phishing attacks often result in direct financial theft. For individuals, this might mean stolen credit card numbers or unauthorized transfers from bank accounts. For businesses, phishing can lead to wire fraud, payroll diversion, or invoice scams — often costing companies millions of dollars, especially when high-level executives are targeted in business email compromise (BEC) schemes.
If a phishing attack gives an attacker access to a company’s internal systems, it can result in the theft of customer records, employee information, intellectual property, or sensitive emails. These breaches can disrupt business operations, expose trade secrets, and violate data protection laws, leading to fines and lawsuits.
Companies that fall victim to phishing attacks often suffer serious damage to their reputation. Customers may lose trust in the company’s ability to protect their information, partners may reconsider doing business, and the brand may be publicly criticized in the media. Rebuilding reputation can take years — and in some cases, the business may never fully recover.
Operational Downtime: Systems may be taken offline to contain the breach.
Legal Consequences: Non-compliance with GDPR, HIPAA, etc., can lead to lawsuits.
Internal Distrust: Employees may lose confidence in leadership or IT security.
Signup our newsletter to get update information, news, insight or promotions.
Copyright 2025 © Hackanics