Insecure Deserialization
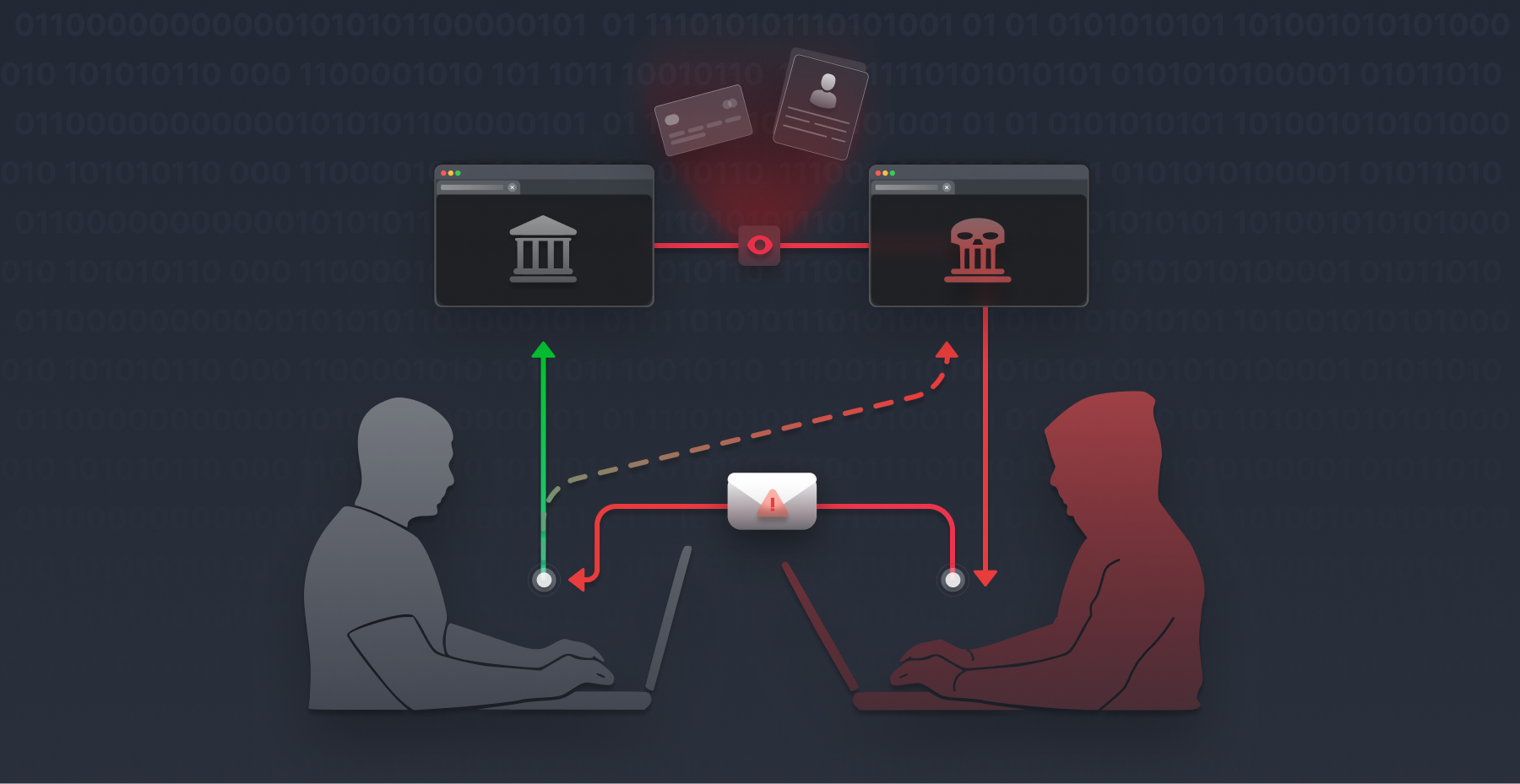
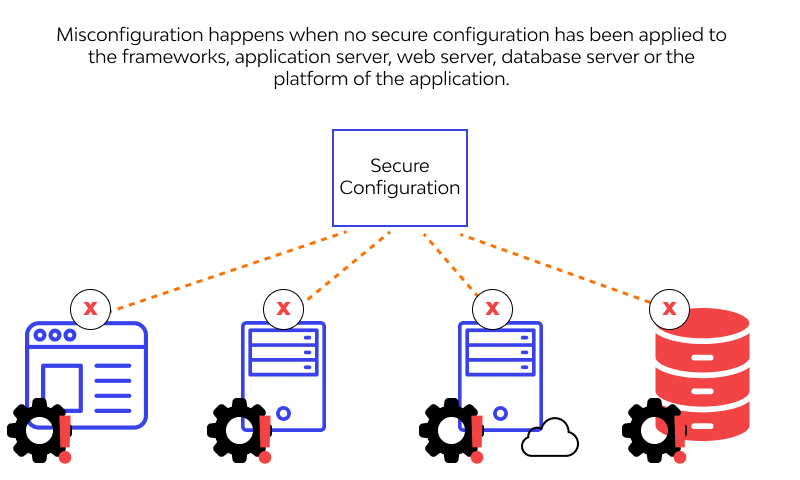
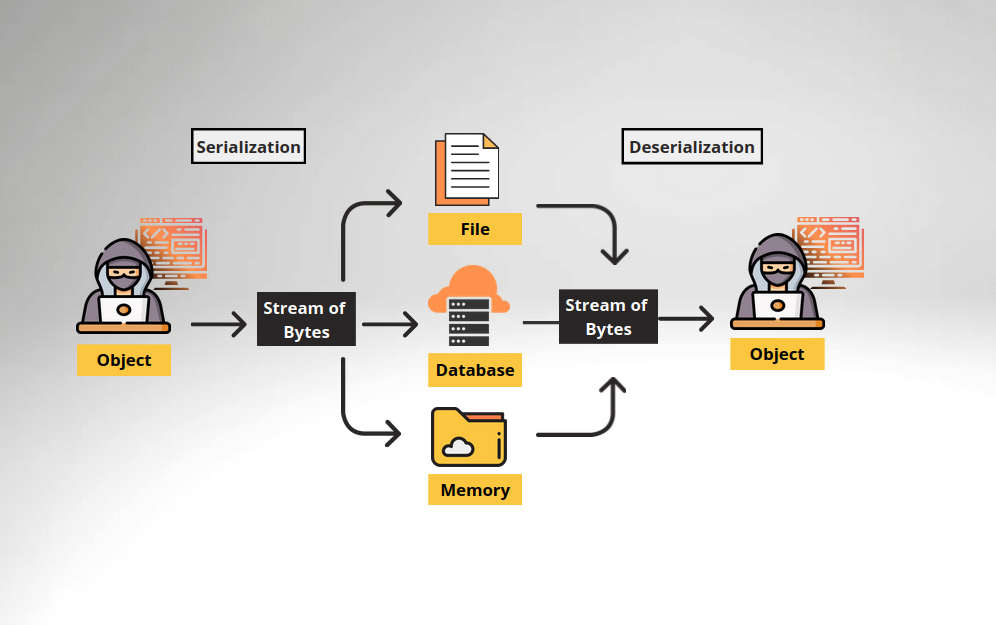
What is Insecure Deserialization? Instagram X-twitter Youtube Insecure Deserialization is a security flaw that happens when an application loads (deserializes) data from an untrusted source without checking it, allowing attackers to modify the data and potentially gain unauthorized access, change