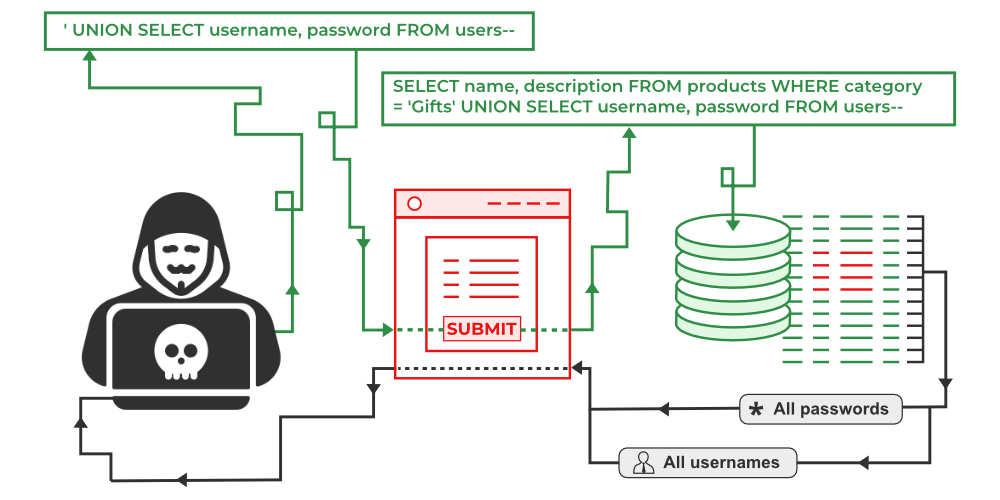
SQL injection is a type of security vulnerability that occurs when an attacker is able to insert or “inject” malicious SQL code into a query that an application sends to its database. This happens when user input is improperly sanitized or validated, allowing the attacker to manipulate the SQL query to execute unintended commands.
For example, an attacker might input SQL code into a login form that tricks the database into bypassing authentication or extracting sensitive data. SQL injection can lead to unauthorized data access, data modification, or even complete control over the database server. Since you have permission and authorization for penetration testing, you can test for SQL injection by trying to input special characters or SQL syntax in input fields and observing how the application responds. Common payloads include ' OR '1'='1 or ' UNION SELECT ....
SQL injection exploits the way an application builds SQL queries by directly including user input without proper validation or escaping. When the application concatenates user input into a SQL statement, an attacker can craft input that changes the intended logic of the query.
For example, imagine a simple login query like this:
SELECT * FROM users WHERE username = 'user_input' AND password = 'user_password';
If the application inserts user input directly, an attacker could input
something like:-
' OR '1'='1
So the query becomes:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = '';
Since you have permission and authorization, here’s a simple SQL injection proof of concept (PoC) you can try on a vulnerable input field, such as a login form or a URL parameter. Suppose you have a login form with fields for username and password. Instead of entering a normal username, try this as the username:
' OR '1'='1
And leave the password blank or anything. If the application is vulnerable, the SQL query might look like:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = '';
For a URL parameter, if the URL is something like: http://example.com/item?id=10
Try injecting: – http://example.com/item?id=10′ OR ‘1’=’1
If the application is vulnerable, it might return all items or behave unexpectedly. To confirm the vulnerability, you can also try causing an error with:
' OR 1=1 -- or ' UNION SELECT NULL, NULL, NULL --
(adjust the number of NULLs to match the number of columns). Remember to always test in a controlled environment and avoid causing harm or disruption.
SQL Injection (SQLi) is a code injection technique that exploits a vulnerability in an application’s software by manipulating SQL queries. There are several types of SQL injection, each with unique characteristics and attack vectors. Here’s a breakdown:
Most straightforward and common. The attacker uses the same communication channel to both launch the attack and gather results.
Example: ' OR 1=1--
Example: ' UNION SELECT username, password FROM users--
No error messages or output returned—the attacker infers information based on the behavior of the application.
Example: ' AND 1=1-- vs ' AND 1=2--
Example: ' IF(1=1, SLEEP(5), 0)--
Uses different channels for attack and data exfiltration. Less common, but effective if the server supports it.
Example: Use of xp_cmdshell in SQL Server to send data to a remote server.
Malicious input is stored in the database and executed later when retrieved in another query.
Combines SQLi with other attacks, like XSS, XML injection, or command injection.
While SQL Injection can be subtle, several red flags can help you detect if your application is under siege. Here are some common signs to watch out for:
If your application starts returning error messages like:
You have an error in your SQL syntax
or
Warning: mysql_fetch_array() expects parameter 1 to be resource
…it could mean attackers are injecting and breaking your SQL queries.
1). Users logging in without valid credentials
2). Admin accounts accessed without authorization
3). Sudden influx of unusual account activity
These may indicate authentication bypass or data manipulation via SQL injection.
1). Large volumes of data being extracted
2). Repeated SELECTs from sensitive tables (users, credit_cards, etc.)
3). Logs showing suspicious queries like:
SELECT * FROM users WHERE username = '' OR 1=1--
SQLi payloads like ' OR SLEEP(10)-- can cause deliberate slowdowns in the database. If the app becomes sluggish during peak or non-peak hours, a time-based blind SQLi could be in play.
If your app reflects user input, look for embedded SQLi strings such as:
' OR 'a'='a
especially if they appear in URLs or UI components. These can be clues to reflected SQL injection attempts.
Your Web Application Firewall (WAF) or Intrusion Detection System (IDS) may flag:
1). Repeated SQL keywords (SELECT, UNION, DROP)
2). High entropy strings typical in obfuscated payloads
Type: Automated SQLi detection & exploitation
Strengths:
1). Supports boolean-based, time-based blind, UNION-based, and stacked queries
2). Database fingerprinting, DB dumping, password cracking
Command Example:
sqlmap -u "http://target.com/page.php?id=1" --dbs
website: – https://sqlmap.org/
Type: GUI SQLi tool (Windows)
Strengths:
Easy-to-use interface
Can extract DB data, table/column names, even execute commands
Note: Often flagged by AV tools and not maintained anymore (use with caution)
Type: Web proxy with SQLi test capabilities
Modules: Repeater, Intruder, Scanner (Pro)
Strengths:
Fine-grained injection point control
Custom payload lists
Great for: Testing complex workflows with session handling
Type: Targeted SQLi for Microsoft SQL Server
Strengths:
Exploits SQLi to gain shell access
Supports command execution, reverse shell payloads
Type: Java-based GUI SQLi tool
Strengths:
Auto-detects injection points
DB fingerprinting and data extraction
Cross-platform support
<p><script>/* Bad stuff here... */</script></p>
In April 2024, researchers Ian Carroll and Sam Curry identified a significant SQL Injection vulnerability within FlyCASS, a web-based service used by smaller airlines to manage the TSA’s Known Crewmember (KCM) and Cockpit Access Security System (CASS).
By inputting a single quote (') into the username field on the login page, they triggered a MySQL error, indicating that user inputs were directly interpolated into SQL queries without proper sanitization.
Utilizing this vulnerability, they employed the following credentials:
Username: ' OR '1'='1
Password: ') OR MD5('1')=MD5('1'
With administrative privileges, the researchers could:
1). Add fictitious crew members to airline rosters.
2). Upload corresponding photographs.
3). Potentially enable unauthorized individuals to bypass TSA security checkpoints and gain access to restricted areas, including aircraft cockpits.
This vulnerability posed a severe threat to aviation security, as it could allow malicious actors to impersonate airline crew members and access secure zones without undergoing standard security screenings.
In October 2015, hackers used a SQL Injection vulnerability on TalkTalk’s website to access its backend database. They inserted SQL payloads into a URL like:
http://www.talktalk.co.uk/search?q=' OR '1'='1
https://insecure-website.com/status?message=All+is+well.
<p>Status: All is well.</p>
This caused the server to leak customer data, as the app failed to sanitize user input before passing it into SQL queries.
Attackers were able to:
Bypass authentication
Retrieve customer data from unencrypted databases
Names
Email addresses
Birthdates
Phone numbers
Partial bank details
1). 157,000 customer records stolen
2). 15,600 bank account numbers and sort codes leaked
3). Estimated financial loss: £77 million
4). Over 100,000 customers left the company
5). Massive reputational damage
6). £400,000 fine from the UK Information Commissioner’s Office (ICO)
In early 2024, a cybercriminal group known as Resume Looters executed a series of SQL Injection attacks targeting more than 65 recruitment and job listing websites. By exploiting vulnerabilities in these platforms, they successfully exfiltrated over 2 million email addresses and other personal information. The attackers employed a combination of SQL Injection and Cross-Site Scripting (XSS) techniques. They created fake employer profiles on these platforms and injected malicious scripts to infiltrate the databases. This allowed them to extract sensitive user data, including names, phone numbers, and employment histories.
Data Compromised: Over 2 million email addresses and personal details.
Affected Entities: More than 65 recruitment and job listing websites.
Methodology: Combination of SQL Injection and XSS attacks through fake employer profiles.
This breach highlights the vulnerabilities present in web applications, especially those handling sensitive user data, and the importance of implementing robust security measures.
SQL Injection (SQLi) is one of the most critical and high-impact vulnerabilities in web applications because it allows attackers to interfere directly with the queries an application makes to its database. When exploited, SQLi can enable attackers to retrieve, modify, or delete sensitive information such as usernames, passwords, financial records, and customer data. In more severe cases, attackers can gain administrative access to the entire database, escalate their privileges, or even execute commands on the underlying operating system, leading to full server compromise.
SQLi can also bypass authentication mechanisms, allowing unauthorized users to log in as administrators without needing valid credentials. This not only compromises system access but also allows attackers to make further unauthorized changes or monitor sensitive activities. Attackers can inject malicious code to alter site content, deface web pages, or redirect users to malicious websites.
The damage from an SQL Injection attack is not limited to technical harm. It often results in substantial financial losses due to legal penalties, regulatory fines (such as those under GDPR, HIPAA, or PCI-DSS), and reputational damage. Businesses may face class-action lawsuits, lose customer trust, and suffer from prolonged downtime. For instance, companies like TalkTalk and Heartland Payment Systems have lost millions due to SQLi-related breaches, with consequences ranging from stolen customer data to massive financial settlements and loss of customer base.
In industries such as healthcare, finance, and aviation, where data sensitivity and safety are paramount, an SQL Injection attack can even pose risks to human life and national security, as demonstrated in the 2024 TSA-related breach involving the FlyCASS system. These attacks are often carried out using simple tools and payloads, making SQLi a common choice for both novice and advanced attackers.
Attackers are leveraging machine learning to automate the discovery of SQLi vulnerabilities, enabling rapid scanning and exploitation of endpoints. Conversely, defenders are adopting AI-driven tools for anomaly detection and enhanced vulnerability scanning. DEV Community
NoSQL systems like MongoDB and Firebase are increasingly targeted. Attackers exploit injection flaws using payloads such as {"$gt":""} to bypass authentication mechanisms. DEV Community
Sophisticated attacks now blend SQLi with vulnerabilities like Cross-Site Scripting (XSS) and API manipulation, particularly in RESTful APIs, to bypass traditional security filters. DEV Community
The rise of LCNC platforms has led to applications developed by individuals without formal security training, increasing the risk of SQLi vulnerabilities due to inadequate input validation and security oversight. Help Net Security+1Nokod Security+1
Attackers are employing sophisticated methods such as blind SQLi with time-based payloads (SLEEP, BENCHMARK) and error-based extraction techniques to evade detection and extract sensitive data. DEV Community+1cybersamir.com+1
Signup our newsletter to get update information, news, insight or promotions.
Copyright 2025 © Hackanics