The Hackanics Threat Intel Blog
Stay informed with expert insights, practical tips, and the latest trends in cybersecurity, training, and digital defense.
Latest Blogs & Articles
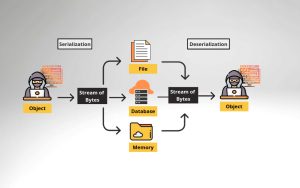
What is Insecure Deserialization? Instagram X-twitter Youtube Insecure Deserialization is a security flaw that happens…
What is Server-Side Request Forgery (SSRF)? Instagram X-twitter Youtube Server-Side Request Forgery (SSRF) is a…
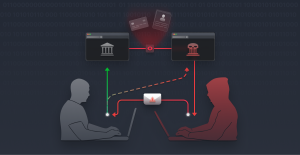
What is Cross-Site Request Forgery (CSRF)? Instagram X-twitter Youtube CSRF tricks an authenticated user into…
What is Threat Detection and Response (TDR) Instagram X-twitter Youtube Threat Detection and Response (TDR)…
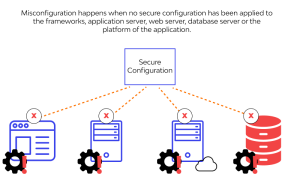
What is Security Misconfiguration Instagram X-twitter Youtube Security misconfiguration is any error or vulnerability present in…
What is BROKEN ACCESS CONTROL ? Instagram X-twitter Youtube Broken access control is a security…
What is sql injection Instagram X-twitter Youtube SQL injection is a type of security vulnerability…
What is Phishing Attack Instagram X-twitter Youtube A phishing attack is a cybercrime in which…
What is cross-site scripting (XSS) Instagram X-twitter Youtube Cross-site scripting (also known as XSS) is…